Win10 NAGA TRINITY driver bug : 0x139_3_CORRUPT_LIST_ENTRY_mouclass!MouseClassDequeueRead
FYI: just in case if there's a bug fix for
FAILURE_BUCKET_ID: 0x139_3_CORRUPT_LIST_ENTRY_mouclass!MouseClassDequeueRead
13: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KERNEL_SECURITY_CHECK_FAILURE (139)
A kernel component has corrupted a critical data structure. The corruption
could potentially allow a malicious user to gain control of this machine.
Arguments:
Arg1: 0000000000000003, A LIST_ENTRY has been corrupted (i.e. double remove).
Arg2: ffffc8838a8edb00, Address of the trap frame for the exception that caused the BugCheck
Arg3: ffffc8838a8eda58, Address of the exception record for the exception that caused the BugCheck
Arg4: 0000000000000000, Reserved
Debugging Details:
------------------
...
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 7139
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 8922
Key : Analysis.IO.Other.Mb
Value: 21
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 33
Key : Analysis.Init.CPU.mSec
Value: 4030
Key : Analysis.Init.Elapsed.mSec
Value: 57675
Key : Analysis.Memory.CommitPeak.Mb
Value: 107
Key : Bugcheck.Code.DumpHeader
Value: 0x139
Key : Bugcheck.Code.KiBugCheckData
Value: 0x139
Key : Bugcheck.Code.Register
Value: 0x139
Key : FailFast.Name
Value: CORRUPT_LIST_ENTRY
Key : FailFast.Type
Value: 3
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
FILE_IN_CAB: MEMORY.DMP
BUGCHECK_CODE: 139
BUGCHECK_P1: 3
BUGCHECK_P2: ffffc8838a8edb00
BUGCHECK_P3: ffffc8838a8eda58
BUGCHECK_P4: 0
TRAP_FRAME: ffffc8838a8edb00 -- (.trap 0xffffc8838a8edb00)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffffc8838a8edd00 rbx=0000000000000000 rcx=0000000000000003
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800803a44ed rsp=ffffc8838a8edc98 rbp=ffffc8838a8edd10
r8=ffffb68fdf5eba58 r9=ffffc8838a8edde0 r10=fffff80062cda3d0
r11=fffff800803a4be0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac pe cy
mouclass!MouseClassDequeueRead+0x51:
fffff800`803a44ed cd29 int 29h
Resetting default scope
EXCEPTION_RECORD: ffffc8838a8eda58 -- (.exr 0xffffc8838a8eda58)
ExceptionAddress: fffff800803a44ed (mouclass!MouseClassDequeueRead+0x0000000000000051)
ExceptionCode: c0000409 (Security check failure or stack buffer overrun)
ExceptionFlags: 00000001
NumberParameters: 1
Parameter[0]: 0000000000000003
Subcode: 0x3 FAST_FAIL_CORRUPT_LIST_ENTRY
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
PROCESS_NAME: System
ERROR_CODE: (NTSTATUS) 0xc0000409 - The system detected an overrun of a stack-based buffer in this application. This overrun could potentially allow a malicious user to gain control of this application.
EXCEPTION_CODE_STR: c0000409
EXCEPTION_PARAMETER1: 0000000000000003
EXCEPTION_STR: 0xc0000409
STACK_TEXT:
ffffc883`8a8ed7d8 fffff800`62e0d329 : 00000000`00000139 00000000`00000003 ffffc883`8a8edb00 ffffc883`8a8eda58 : nt!KeBugCheckEx
ffffc883`8a8ed7e0 fffff800`62e0d890 : 00004970`2c6d2ce8 fffff800`7aaa2285 00000000`00000001 00001f80`00c8026b : nt!KiBugCheckDispatch+0x69
ffffc883`8a8ed920 fffff800`62e0b85d : ffffb68f`dfdd5010 fffff800`8903eed8 00000000`00000000 fffff800`62c2a715 : nt!KiFastFailDispatch+0xd0
ffffc883`8a8edb00 fffff800`803a44ed : fffff800`803a4c7a ffffb68f`df5eb9c0 00000000`00000103 ffffb68f`dfe0a988 : nt!KiRaiseSecurityCheckFailure+0x31d
ffffc883`8a8edc98 fffff800`803a4c7a : ffffb68f`df5eb9c0 00000000`00000103 ffffb68f`dfe0a988 00000000`00000000 : mouclass!MouseClassDequeueRead+0x51
ffffc883`8a8edca0 fffff800`80361c59 : ffffc883`8a8eddf0 ffffc883`8a8ede08 ffffc883`8a8edde0 ffffc883`8a8edde0 : mouclass!MouseClassServiceCallback+0x9a
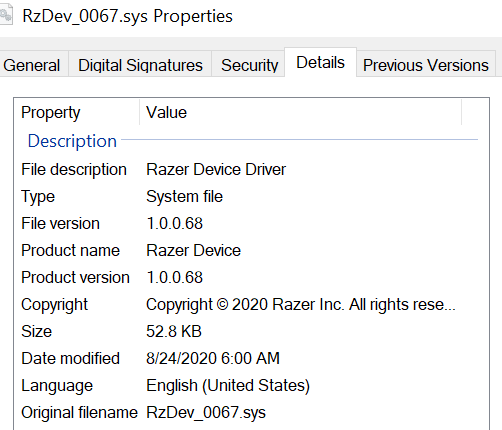
ffffc883`8a8edd40 fffff800`80361d69 : ffffb68f`dfdb4b30 ffffb68f`dff384c0 00000000`00000000 00000000`00000001 : RzDev_0067+0x1c59
ffffc883`8a8edd70 fffff800`803c4e9b : 00000000`00000001 00000000`00000001 00000000`00000004 ffffb68f`dff33ef8 : RzDev_0067+0x1d69
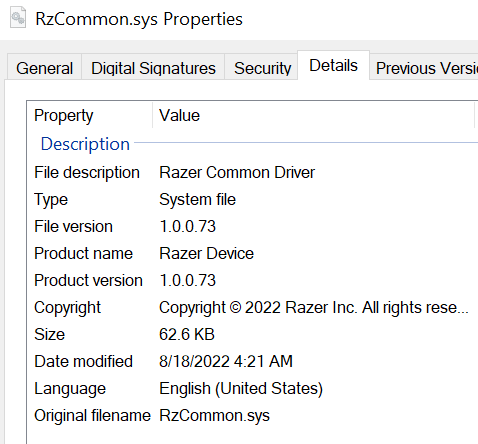
ffffc883`8a8eddb0 fffff800`803c40ef : ffffb68f`d3902dc0 00000000`00000000 ffffb68f`dfe10a20 ffffb68f`dfda0b90 : RzCommon+0x4e9b
ffffc883`8a8ee160 fffff800`803c57a8 : ffffb68f`dfdd5010 ffffb68f`dff33ee0 ffffb68f`dff33ef8 ffffc883`8a8ee5a4 : RzCommon+0x40ef
ffffc883`8a8ee450 fffff800`803618ea : 00000000`000b000b ffffb68f`f0fdc1a0 00000000`000b000b ffffb68f`dfe10060 : RzCommon+0x57a8
ffffc883`8a8ee480 fffff800`80361c05 : 00000000`00000000 ffffc883`8a8ee5b0 00000000`00000000 fffff800`00000000 : RzDev_0067+0x18ea
ffffc883`8a8ee4b0 fffff800`80363149 : ffffb68f`dfe14510 ffffb68f`dff33ee0 ffffb68f`dff33ef8 fffff800`899523c4 : RzDev_0067+0x1c05
ffffc883`8a8ee4f0 fffff800`803621ab : ffffb68f`dff33ef0 00000000`00000000 00000000`ffffffff 00000000`00000001 : RzDev_0067+0x3149
ffffc883`8a8ee520 fffff800`80383aa8 : 00000000`00000002 ffffc883`8a8ee5b8 ffffb68f`db86f010 ffffb68f`dff33d80 : RzDev_0067+0x21ab
ffffc883`8a8ee560 fffff800`62c1fece : 00000000`00000000 00000000`00000000 00000000`00000001 00000000`00000000 : mouhid!MouHid_ReadComplete+0x758
ffffc883`8a8ee600 fffff800`62c1fd97 : 00000000`00000000 ffffb68f`dd0c7806 ffffb68f`dfd664d0 00000000`00000000 : nt!IopfCompleteRequest+0x11e
ffffc883`8a8ee6f0 fffff800`8990b345 : ffffb68f`e6196358 ffffb68f`dfe10102 00000000`00000000 00000000`00000009 : nt!IofCompleteRequest+0x17
ffffc883`8a8ee720 fffff800`8990ac3d : ffffb68f`dfe101d0 ffffb68f`dfe10102 ffffb68f`dfe101d0 00000000`00000009 : HIDCLASS!HidpDistributeInterruptReport+0x3f5
ffffc883`8a8ee820 fffff800`62c1fece : ffffb68f`dfdd4010 ffffb68f`dfdd4010 ffffc883`8a8ee901 fffff800`80f04701 : HIDCLASS!HidpInterruptReadComplete+0x37d
ffffc883`8a8ee8c0 fffff800`62c1fd97 : 00000000`00000001 00000000`00000000 ffffb68f`dfdd3bc0 00000000`00000002 : nt!IopfCompleteRequest+0x11e
ffffc883`8a8ee9b0 fffff800`64bd811a : 00000000`00000000 ffffb68f`df477db0 ffffb68f`dfdd4010 00000000`00000001 : nt!IofCompleteRequest+0x17
ffffc883`8a8ee9e0 fffff800`64bd7eb1 : 00000000`00000002 00000000`00000000 ffffb68f`dfdd4010 00000000`00000000 : Wdf01000!FxRequest::CompleteInternal+0x23a [minkernel\\wdf\\framework\\shared\\core\\fxrequest.cpp @ 869]
ffffc883`8a8eea70 fffff800`64bd9249 : ffffb68f`d2137370 ffffb68f`d2137370 00000000`00000001 fffff800`8036334c : Wdf01000!imp_WdfRequestCompleteWithInformation+0xa1 [minkernel\\wdf\\framework\\shared\\core\\fxrequestapi.cpp @ 571]
ffffc883`8a8eead0 fffff800`64bdc854 : 00004970`2dec8c88 ffffb68f`d2137370 ffffb68f`d2137370 00000000`c0000001 : Wdf01000!FxRequestBase::CompleteSubmitted+0xe9 [minkernel\\wdf\\framework\\shared\\core\\fxrequestbase.cpp @ 530]
ffffc883`8a8eeb60 fffff800`62d569b6 : ffffb68f`df46ede0 ffffb68f`dfdd4002 ffffb68f`dfdd4010 ffffc883`8a8eec50 : Wdf01000!FxIoTarget::_RequestCompletionRoutine+0xe4 [minkernel\\wdf\\framework\\shared\\targets\\general\\fxiotarget.cpp @ 2448]
ffffc883`8a8eebd0 fffff800`62c1fece : ffffb68f`dfdd4010 ffffc883`8a8eec89 ffffb68f`df46ede0 ffffb68f`dfdd47a3 : nt!IopUnloadSafeCompletion+0x56
ffffc883`8a8eec00 fffff800`62c1fd97 : 00000000`00000001 00000000`00000000 ffffb68f`dfe219b0 00000000`00000002 : nt!IopfCompleteRequest+0x11e
ffffc883`8a8eecf0 fffff800`64bd811a : 00000000`00000000 ffffb68f`d3902dc0 ffffb68f`dfdd4010 ffffc883`8a8eedd0 : nt!IofCompleteRequest+0x17
ffffc883`8a8eed20 fffff800`64bd5bbf : ffffb68f`dd6bfa02 ffffb68f`f1324a60 ffffb68f`dfdd4010 00000000`00000000 : Wdf01000!FxRequest::CompleteInternal+0x23a [minkernel\\wdf\\framework\\shared\\core\\fxrequest.cpp @ 869]
ffffc883`8a8eedb0 fffff800`7aa0c1ed : 00000000`ffffff02 ffffb68f`dd6bf950 ffffb68f`dfe21d90 ffffb68f`dfe21d90 : Wdf01000!imp_WdfRequestComplete+0x8f [minkernel\\wdf\\framework\\shared\\core\\fxrequestapi.cpp @ 436]
ffffc883`8a8eee10 fffff800`7aa0c0b1 : ffffb68f`dd6bfaf0 00000000`00000008 ffffb68f`dd6bfb80 ffffc883`8a8ef028 : USBXHCI!Bulk_Transfer_CompleteCancelable+0xc9
ffffc883`8a8eee70 fffff800`7aa0bea0 : 00000000`00000004 ffffc883`8a8eefe0 00000000`00000000 ffffb68f`dfe0fa60 : USBXHCI!Bulk_ProcessTransferEventWithED1+0x1fd
ffffc883`8a8eef20 fffff800`7aa06911 : 00000000`00000004 ffffc883`8a8eeff8 00000000`00000008 ffffc883`8a8ef000 : USBXHCI!Bulk_EP_TransferEventHandler+0x10
ffffc883`8a8eef50 fffff800`7aa06445 : 00000000`00000780 00004970`2c6ec300 ffffb68f`dbfff4c0 ffffb68f`dfe036e0 : USBXHCI!Endpoint_TransferEventHandler+0xb1
ffffc883`8a8eefb0 fffff800`7aa0611c : ffffb68f`dd3bd368 ffffcc01`cccc0180 00004970`2c6e1538 ffffc883`8a8ef3f4 : USBXHCI!Interrupter_DeferredWorkProcessor+0x315
ffffc883`8a8ef0b0 fffff800`64bd38f6 : ffffc883`8a8ef420 00000000`00000000 00000000`00000000 00000000`00000000 : USBXHCI!Interrupter_WdfEvtInterruptDpc+0xc
ffffc883`8a8ef0e0 fffff800`62c348fe : ffffcc01`cccc3240 ffffb68f`d14db000 ffffc883`8a8ef3e0 ffffcc01`00000002 : Wdf01000!FxInterrupt::_InterruptDpcThunk+0xa6 [minkernel\\wdf\\framework\\shared\\irphandlers\\pnp\\km\\interruptobjectkm.cpp @ 410]
ffffc883`8a8ef120 fffff800`62c33be4 : 00000000`00000000 fffff800`62d2306a 00000000`00140001 00000000`00000000 : nt!KiExecuteAllDpcs+0x30e
ffffc883`8a8ef290 fffff800`62dfdb9e : ffffffff`00000000 ffffcc01`cccc0180 ffffcc01`ccccb540 ffffb68f`e8ea0080 : nt!KiRetireDpcList+0x1f4
ffffc883`8a8ef520 00000000`00000000 : ffffc883`8a8f0000 ffffc883`8a8e9000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x9e
SYMBOL_NAME: mouclass!MouseClassDequeueRead+51
MODULE_NAME: mouclass
IMAGE_NAME: mouclass.sys
STACK_COMMAND: .cxr; .ecxr ; kb
BUCKET_ID_FUNC_OFFSET: 51
FAILURE_BUCKET_ID: 0x139_3_CORRUPT_LIST_ENTRY_mouclass!MouseClassDequeueRead
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {6b5843fa-650f-1f9f-d95b-388440977a32}
Followup: MachineOwner
---------
Sign up
Already have an account? Login
Log in with Razer ID to create new threads and earn badges.
LOG INEnter your E-mail address. We'll send you an e-mail with instructions to reset your password.