This is not necessary just to control my LED functions
This seems a bit Wrong that i paid for this razer naga mouse but am left with your unfair ultimatum for full control over a simple things like the L.E.D. Function . Which even though was unspoken by Razer is clearly implied.
"You can have control over this function, But only if we can dump this large amount of Bloat-ware on you computer that far exceeds the the space required for that function and take up a large chunk of you system recourses without a choice of where its installed... so what do you say we got a DEAL ".
when put like that would any one agree to it? probably not. but this is what razer is doing.
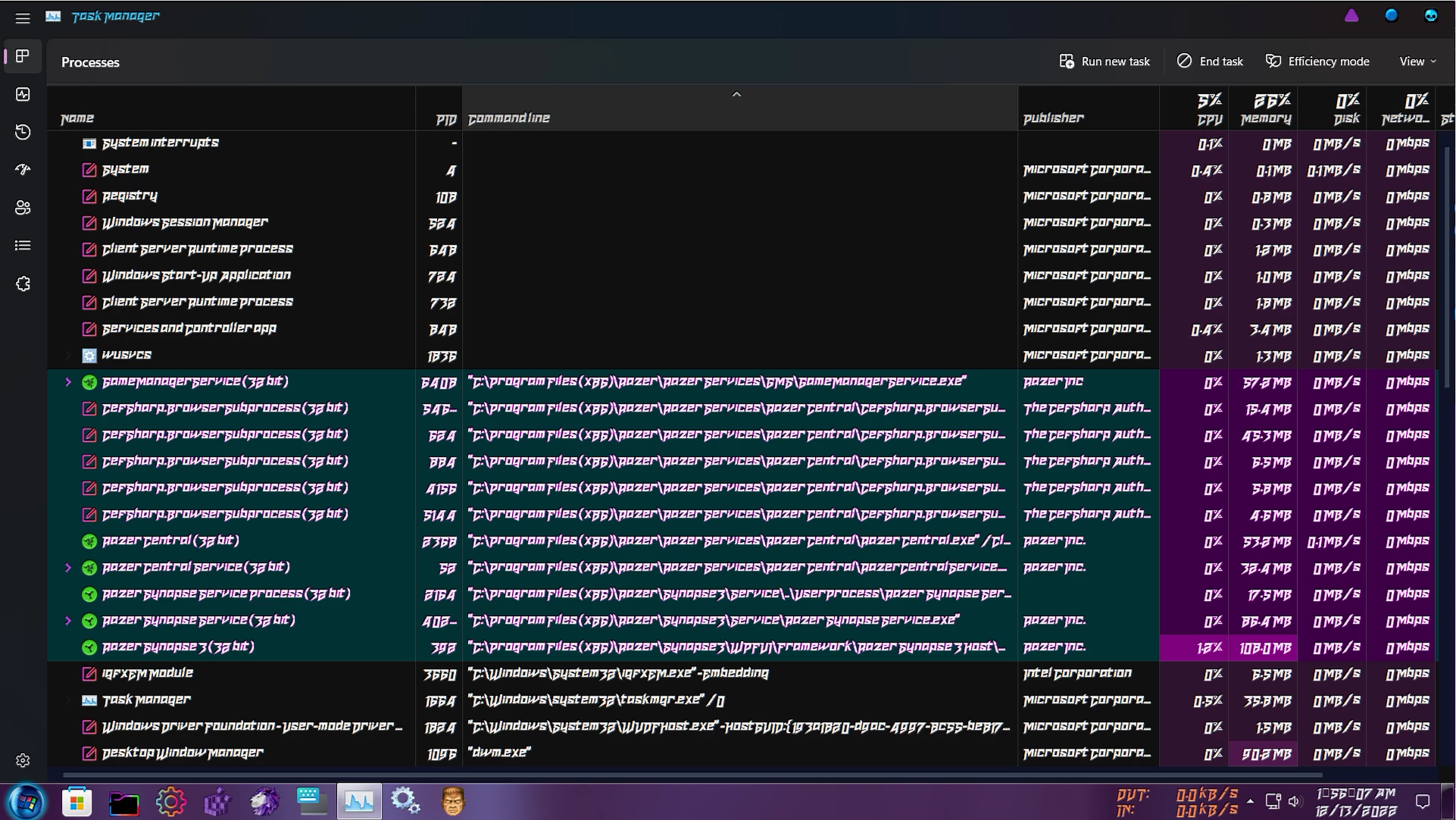
I mean 11 Processes and that's just what's running under razers name I'm sure there's more.
a bit over kill for LED control don't you think especially when I know for a fact the mouse has enough memory to hold the selected LED information. because that's how Logitech stores the LED date and they offer two programs a big over blown resource hungry monster like Synapse and a small stand alone EXE that doesn't require installation that not only lets you edit the LED patterns but the Key bindings as well. once done the mouse stays the way you wanted it and there no Logitech anywhere to be found in the task manager. where razers small program? oh they don't have one.
So what's all that stuff running in the background anyway? that is useless to the user. Well considering they used unfair underhanded method used to force it on the users PC's. its obvious its telemetry and analytical data collecting software.
That's the only type of software I know of that will make a tech company change from your best friend to a raving lunatic just to get it on you machine.
So now i have it brake out the Arduino and play hack the mouse. well until next time!!!!


Reply
Rich Text Editor, editor1
Editor toolbars
Press ALT 0 for help
Sign up
Already have an account? Login
Log in with Razer ID to create new threads and earn badges.
LOG INEnter your E-mail address. We'll send you an e-mail with instructions to reset your password.


